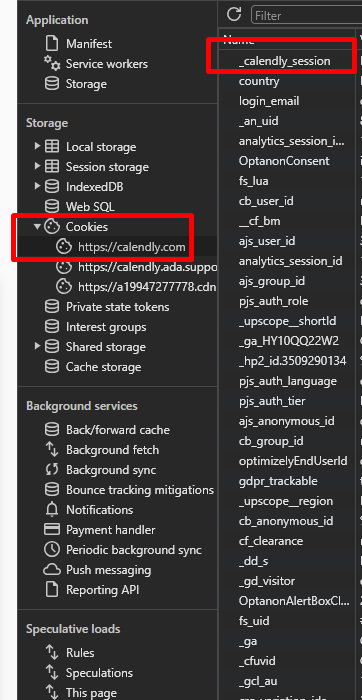
in my product, I have integrated Calendly using oauth2.0.
When user logged in, it stores cookie inside their domain calendly.com.
The problem is when user sign out and again sign in because of those cookies already store, it does not ask for credentials and logged in with previous account automatically.
At the time of logging out, also invoked revoke token endpoint API provided by Calendly.
Question
Logging out with Iauth2.0
Sign up
Already have an account? Login
Not a Calendly user yet? Head on over to Calendly.com to get started before logging into the community.
Employee Login Customer LoginLogin to the community
Not a Calendly user yet? Head on over to Calendly.com to get started before logging into the community.
Employee Login Customer LoginEnter your E-mail address. We'll send you an e-mail with instructions to reset your password.